IP Filtering and Auto-banning
IP Filtering and Auto-Banning are essential tools in keeping out unwanted visitors to your site and are supported in the Professional and Enterprise MFT Editions.
Auto-Banning
Auto-Banning works by automatically banning IP addresses from connecting (for a pre-configured period of time) if they have failed to authenticate a certain number of times within a time period. Except in the Standard Edition, these details can be configured to suit customer preferences.
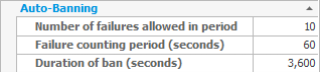
Currently banned IP addresses can be viewed in the monitoring tab of CompleteFTP's manager application.
IP-Filtering
CompleteFTP has a very configurable IP Filtering interface, shown below.
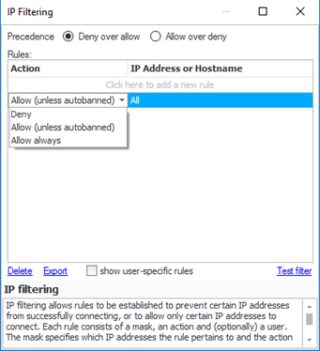
IP filtering operations that are supported include:
