How to configure LDAP users
Background
LDAP (Lightweight Directory Access Protocol) is a protocol used to access and manage directory information services over a network. These directories can store information about users, groups, and other resources, making LDAP a popular choice for authentication and directory lookups in organizations.
Configuration of the LDAP authenticator involves setting up the LDAP server details, user credentials, and query parameters to authenticate users. The form allows you to specify these settings and test the login credentials.
Configuring LDAP in CompleteFTP
LDAP authentication can be configured in the General User Settings dialog, accessed from the Users panel. The LDAP authenticator must be enabled and configured via the 'Configure' link shown below:
Clicking the 'Configure' link will bring up the LDAP Configuration dialog.
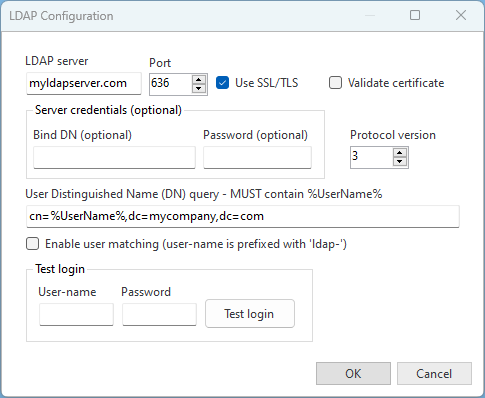
LDAP Configuration Fields
- LDAP Server: Enter the address of the LDAP server. This is the hostname or IP address where the LDAP service is running.
- Port: Enter the port number for the LDAP server. The standard port is 389 for non-SSL connections and 636 for SSL connections.
- Use SSL/TLS: Check this box to use SSL/TLS for secure communication with the LDAP server. This ensures that data exchanged with the LDAP server is encrypted.
- Validate Certificate: Check this box to validate the LDAP server's SSL certificate. This ensures that the server's certificate is trusted and prevents man-in-the-middle attacks. The certificate will be validated against the certificates in the machine's certificates store.
- Bind DN (optional): Enter the Distinguished Name (DN) to bind to the LDAP server, if required. This DN is used to authenticate the LDAP connection and should have the necessary permissions to perform searches in the LDAP directory. The Bind DN format is typically something like "cn=admin,dc=example,dc=com". Many LDAP servers allow anonymous access for authentication, in which case this field should be left blank.
- Bind DN Password: Enter the password for the Bind DN. This password is used to authenticate the Bind DN to the LDAP server. This field is also optional.
- LDAP Version: Select the LDAP protocol version. Typically, version 3 is used.
- User DN Query: Enter the DN query to locate the user in the LDAP directory. This query must include %UserName%, which will be replaced with the actual username during the authentication process. For example, "cn=%UserName%,dc=example,dc=com". This query is crucial for locating the user's DN in the directory and must be accurate to ensure successful authentication.
- Enable User Matching: When enabled, CompleteFTP will match the logged-in user with a CompleteFTP user whose username is prefixed with 'ldap-'. If one is found, that user will be used as the log-in-as user for the session. For example, if the user enters 'user1', user-matching will look for 'ldap-user1'.
- Test Username: Enter a username to test LDAP authentication. This is used to validate that the LDAP configuration is correct.
- Test Password: Enter the password for the test username. This is used to validate that the LDAP configuration is correct.
- Test Login: Once the LDAP server details and query parameters are configured, enter a username and password here to test the authentication settings. Click the 'Test login' button to perform the test.
Valid User-Names
For security reasons, user names must not contain certain special characters that could be used in LDAP injection attacks.
The following characters are prohibited: \ * ( ) / + & | = ! > < ~ - , ; ' " `.
Example User DN Queries
- Basic Query: cn=%UserName%,dc=example,dc=com
- With Organizational Unit: cn=%UserName%,ou=users,dc=example,dc=com
Testing the LDAP Configuration
Once LDAP has been configured and applied to the server, use the test login fields to validate the configuration. Enter a test username and password, then click 'Test login'. If the test is successful, the LDAP configuration is correct. If there are errors, check the LDAP server details and query parameters.
Default User Settings
Users authenticated via LDAP are subject to the settings of the "defaultExtension" user, which may be found in the Users panel. The administrator may enable specific protocols or settings for LDAP user connections.

